Part 1 of 2
Written by Amanda Watson, Office Manager/Marketing Specialist (Portage, IN)
We just had a Cyber Security Class put on by our IT Director, Chris Hatfield. In it, Chris explained about the different kinds of cyber attacks and how to recognize and prevent them from attacking our work computers. Of course, this kind of information is too important to keep all to ourselves, so we wanted to share it with all of you.
The most common attack vectors that we learned about today are:
- Phishing Scams
- Spear Phishing
- Trojan Horse
- Drive-by Downloads
- Watering Hole
- Social Engineering
- WiFi
Today, we’ll discuss the first three of these cyber attack vectors: Phishing Scams, Spear Phishing and the Trojan Horse.
Phishing Scams:
A phishing scam is the act of sending email that falsely claims to be from a legitimate organization. Phishing scams are usually combined with a threat or request for information such as: the impending closure of an account; a balance that is due; or that information is missing from an account. The email will ask the recipient to supply confidential information such as bank account details, PINs or passwords. NEVER SUPPLY THIS TYPE OF INFORMATION. There are two great videos on YouTube you can check out for more information on Phishing Scams:
Phishing Examples:
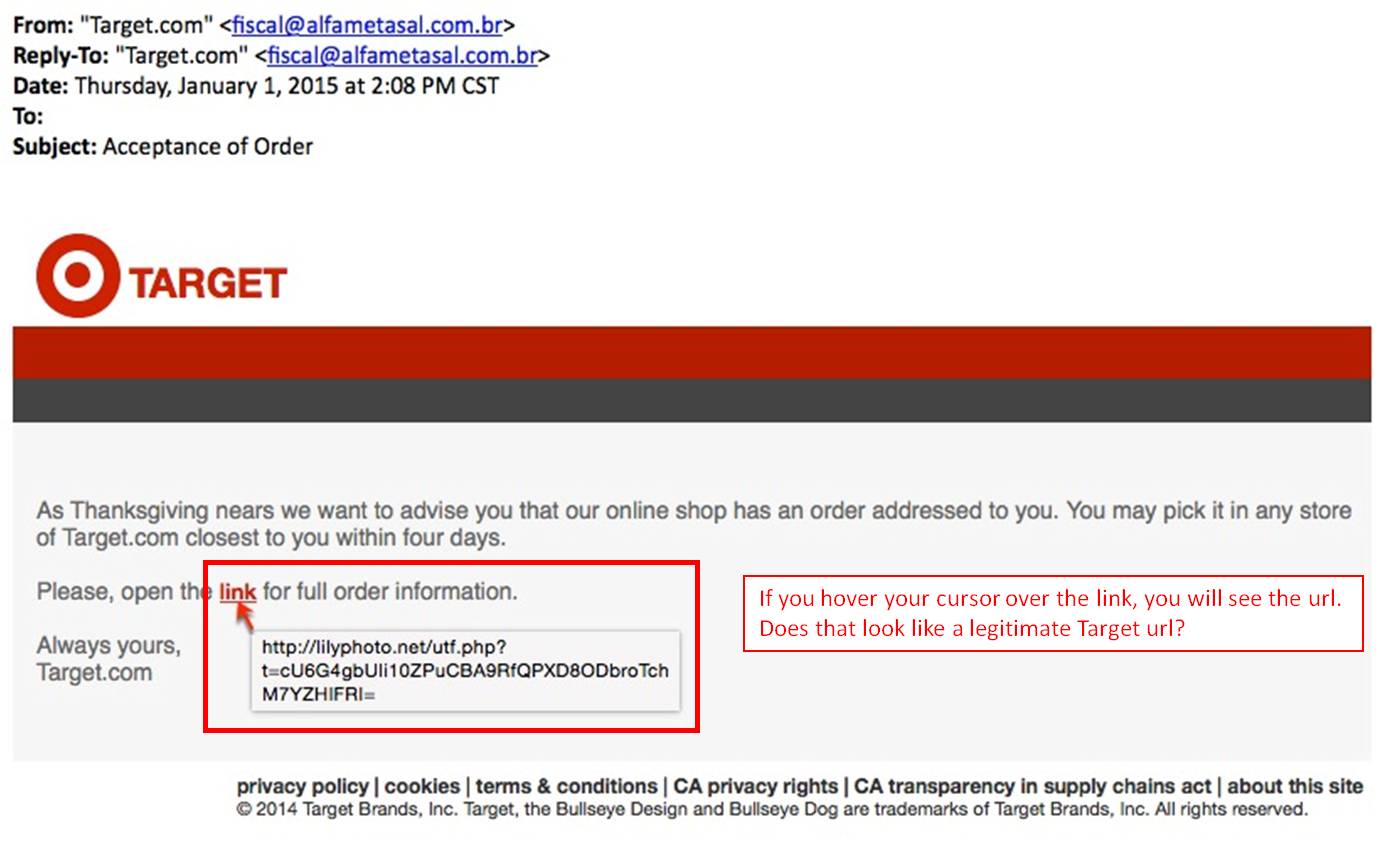
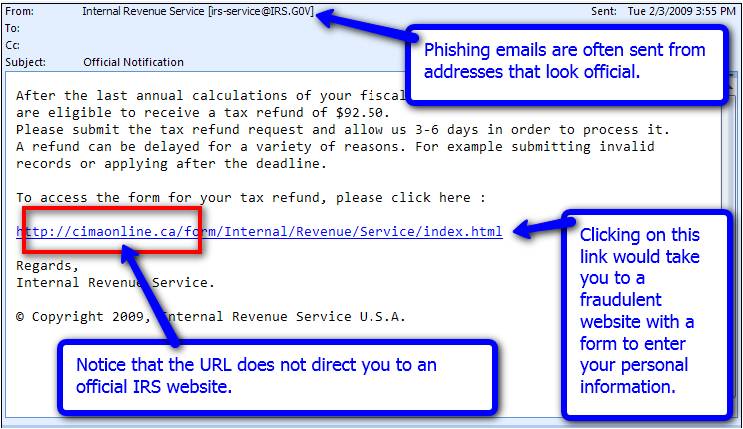
Spear Phishing:
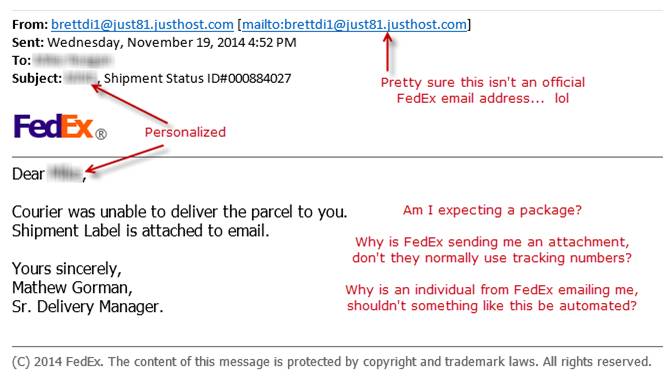
Spear Phishing is a variation on phishing in which hackers send emails to groups of people with specific common characteristics or other identifiers. Spear phishing emails appear to come from a trusted source but are designed to help hackers obtain trade secrets or other classified information. The practice of sending fraudulent emails to extract financial data from computer users for purposes of identity theft, by mimicking a sender that the recipient knows.
If you’re not expecting an email from the sender, don’t click the link. Many times, these emails will be written in a way that lets you know they’re not from your contact; such as they seem to have been written by a person who is not a native English speaker. Always investigate any links in an email to see where they will take before you click; if the link it to a zip file, or a suspicious website, DO NOT OPEN IT. Ask an IT professional if you have any questions — it’s better to be safe than sorry! And here’s a great video to learn more:
Phishing Scams — Don’t Be That Guy — Trend Micro
Trojan Horse:
A Trojan Horse is a program that appears desirable but actually contains something harmful. It can be a destructive program that masquerades as a benign application, a seemingly useful computer program that contains concealed instructions which when activated perform an illicit or malicious action, or a non-replicating computer program planted illegally in another program to do damage locally when the software is activated.
Trojan Horse Examples:
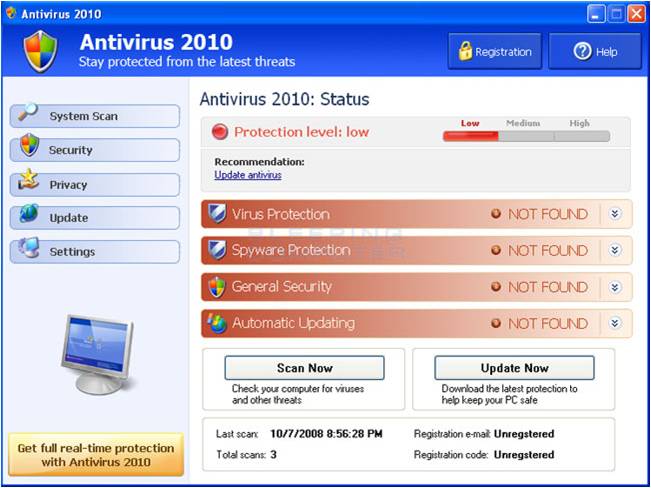
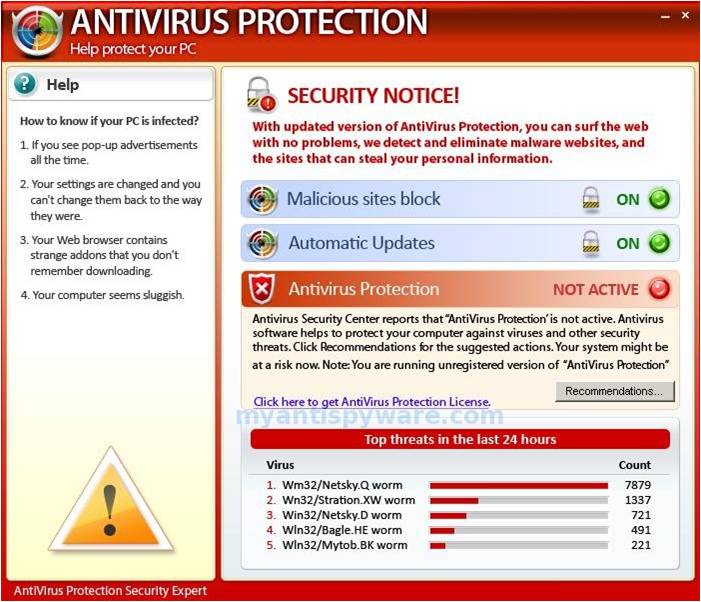
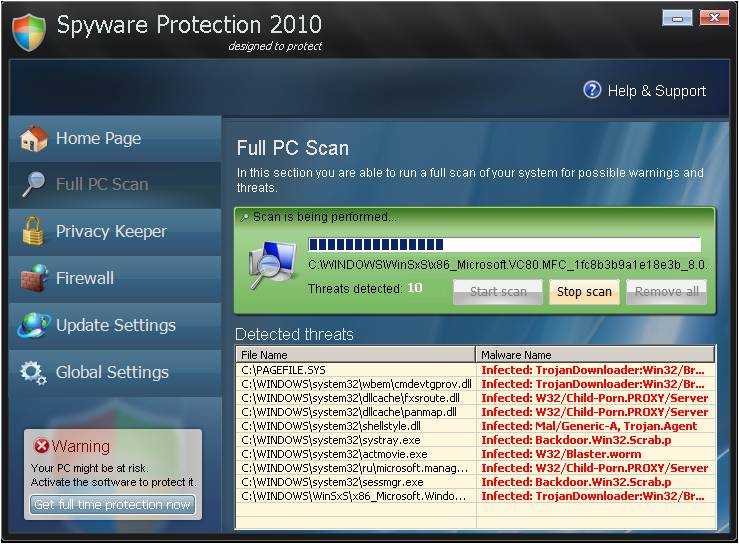
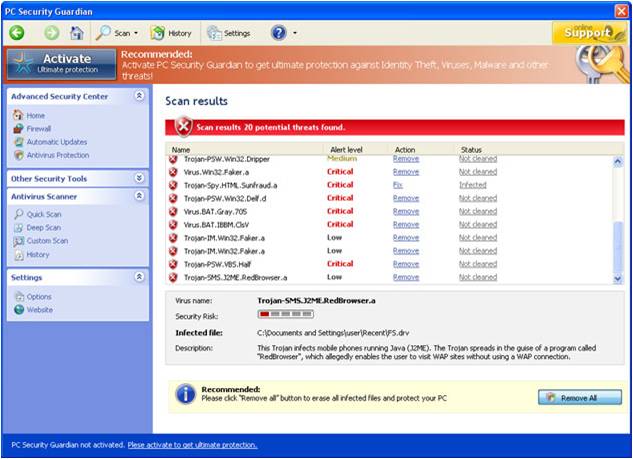
The pop-up will appear on your screen to try to lure you into clicking the action button (i.e. Remove All, Activate, Scan Now). These appear to be legitimate antivirus applications, but will instead infect your computer. Unless you have asked your anti-virus to perform a scan, these types of pop-ups should not appear. And always be sure that the name of the supposed anti-virus program is the same as the actual program you have installed on your computer.
We hope this information helps you identify phishing scams, spear phishing and Trojan horse programs. Click the link below to read Part 2, where we address Drive-by Downloads, Watering Hole, Social Engineering and WiFi attacks.
