Part 2 of 2
Here it is…the exciting conclusion of our series on how to recognize and prevent cyber attacks. In our last post, we covered: Phishing Scams, Spear Phishing and Trojan Horse attacks. Today, we will focus our efforts on:
- Drive-by Downloads
- Watering Hole
- Social Engineering
- WiFi
Drive-by Downloads:
There are many types of drive-by downloads including:
- A download triggered by scripts etc. on a website, without prompting the user, usually for malicious purposes
- An incidence of an unwanted program being automatically downloaded to a computer, often without the user’s knowledge
- A program that is automatically installed in your computer by merely visiting a web site, without having to explicitly click on a link on the page
- Any download to a computer or device that occurs without the owner’s consent
The most famous example of a drive-by download is the Crypto Locker/Crypto Wall. This attack:
- Encrypts local files
- Encrypts server files
- Is pretty much unbreakable
- Is installed from a link in an email or from a website
Drive-by Download Attack Example:
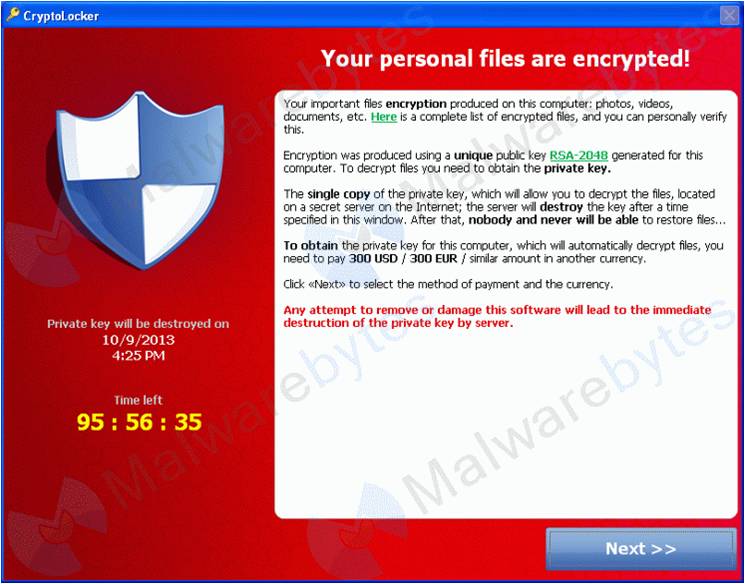
To un-encrypt your files, the hackers send you the message above and require a payment within a certain timeframe before sending you the key. Of course, there is no guarantee that once you send them the money, they’ll actually send you the key so it’s best to practice vigilance in your online activities.
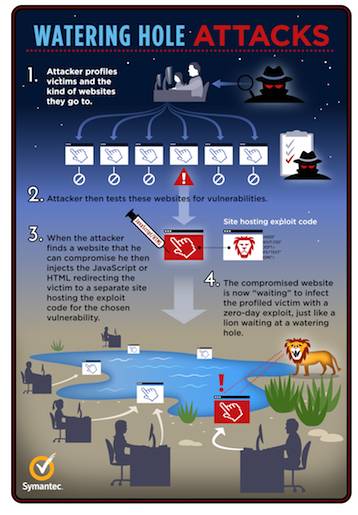
Watering Hole Attack:
A Watering Hole attack occurs when a hacker manipulates a website that is visited and trusted by members of a target group, usually by placing some form of malware on the website whose sole purpose is to infect the website visitor’s computer. When visiting the manipulated website, devices of the target group are infected which allows the hacker to gain access to the information on the computer/network of the computer that visited the infected website.
Watering Hole Explanation:
Social Engineering:
A Social Engineering attack can come from an email, a website and/or a phone call. An email social engineering attack usually comes from a friend (someone you know) who urgently asks for help, usually in the form of money; or an email from a friend that asks you to check out a “way cool link”. However, when you click the link or comply with the email request, you find you’ve been scammed. A great way to prevent this type of attack is to check with your friend in another form of communication to make sure the message has really come from that person. Check the syntax of the email message…is that how your friend usually talks? Since the hacker doesn’t know how you and your friend usually communicate, he/she probably doesn’t know how to write like your friend, which is a major clue to a scam.
In the baiting scenario, you’re offered an amazingly great deal that too good to pass up or a link to watch the latest movie free just by clicking here. If a deal seems too good to be true, it probably is. Finally, there’s the phone call attack where you receive an unsolicited call that asks for personal or company information. Remember, you are the first line of defense against these attacks, never give your personal information over the phone. If you think a phone call may be legit, try contacting a trusted source at the suspect company — if you don’t know anyone, try researching the firm and finding another contact number.
WiFi Attacks:

We decided to cover this because it’s important to know that free WiFi isn’t so free! If you’re using free WiFi, that means other people can use it, too, so you should always assume someone else can be accessing your connection. Never enter confidential information while you’re connected to free WiFi including passwords, banking and credit card information.
Defenses (Review)
The best defenses against any type of cyber attack is you — you can identify suspicious email by verifying links before clicking on them’ not downloading anything you receive from untrusted, unverified source; and generally questioning everything.
- Do you really believe that a Nigerian prince has left you millions of dollars?
- Is that strange looking email really something your (friend/brother/sister/mom/dad) would send to you?
- Is that deal on (whatever website) too good to be true? (It probably is”¦.)
- Do you really have a FedEx or UPS package waiting for you?
- Why did this strange application POP UP on my desktop? Should I click on it? (NO! Call I.T.)
You should also have a secure firewall in place that scans all incoming traffic, email, web traffic and downloads as well as trusted anti-spam, anti-virus and anti-malware software on your computer. Our Holladay Properties computers are protected by our IT department, but you can have all these wonderful protection equipment on your home computer. Ask for recommendations on the best software applications, do you research and find one that works for you. Don’t take risks with your personal information — protect yourself and your company.
Missed the first post? Click here to read Part 1!
